
views
- If you notice apps, purchases, or sent messages on your phone that you didn't initiate, this is a red flag that you may have been hacked.
- If your phone is running hot or the battery is dying quickly, a hacker could be running background processes on your device.
- Changing your passwords can keep hackers out of your personal information.
- If all else fails, factory resetting your phone can completely push a hacker out.
How to Tell If Your iPhone Is Hacked

Your phone feels hotter than normal. If you've noticed that your phone is getting hotter than normal and you haven't changed how you use your phone, this could indicate that there are unauthorized processes running in the background, initiated by a hacker.

Your phone's battery runs out much quicker than it used to. If you are using your phone like normal and you realize the battery is dying faster than before, this could also indicate that there are background processes going on that you didn't initiate.

Your phone's performance has gotten worse. If your phone has slowed down significantly, this could be a sign that a hacker is running background processes on your phone. As a phone gets older it may slow down, but you shouldn't see a drastic drop in performance overnight.
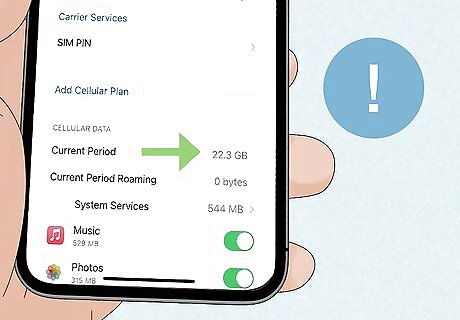
Your phone is using more data than it usually does. In your iPhone settings, under Cellular, you can check how much data your phone has used during your current billing period. If this number is much higher than normal, or you've noticed a huge spike in your cell phone bill, hackers could be using your iPhone's data without your knowledge.

There are apps on your phone that you didn't install. If you notice an app on your phone that you didn't install, this could have been placed there by a hacker. These apps may not appear on your home screen, so make sure to check all of the apps installed on your phone in your App Library.
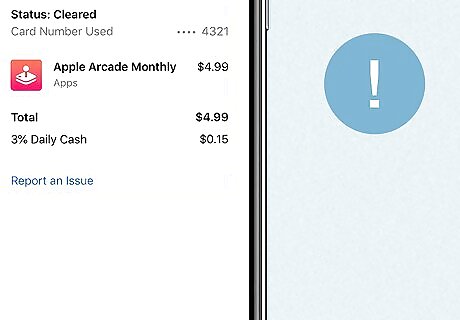
There are unauthorized purchases made on your Apple ID. If you notice strange charges on your credit card or bank statement, or notifications from Apple Pay, investigate them immediately. Some hackers may test the waters with small purchases before pulling out as much money as possible from your accounts.
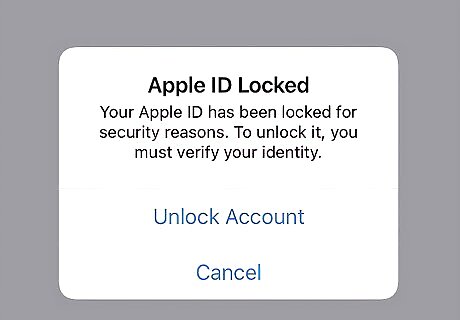
You're locked out of your Apple ID. If you get emails about your Apple ID that detail account changes or sign-ins that you didn't initiate, this is a clear sign that a hacker has gotten access to your account.

The camera or microphone on your phone turn on by themselves. Some hackers may try to use your phone camera or microphone to try and steal information from you. If you notice the camera or microphone on your iPhone turn on without you initiating it, this could mean a hacker has gotten into your phone. On the top of your phone screen, a colored dot will appear if the camera or microphone are in use. A green dot means an app is using the camera, and an orange dot means an app is using the microphone.

Messages are being sent from your phone that you didn't send. If your contacts let you know that you've been sending strange messages, this could be the work of a hacker. You can also check your text messages to see if there are messages that your phone has sent that you don't recall sending.
What to Do If Your iPhone Has Been Hacked

Remain calm. Getting hacked can be a scary experience, but there are a number of ways you can push the hacker out of your phone.
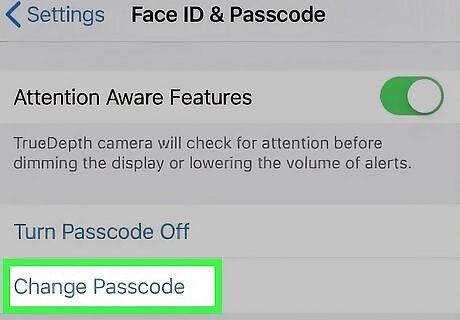
Change your passwords. You should definitely change your Apple ID password if you suspect you've been hacked, but changing all of your passwords would be the safest bet. Consider using a password manager to help create complex passwords that you don't have to try and remember.
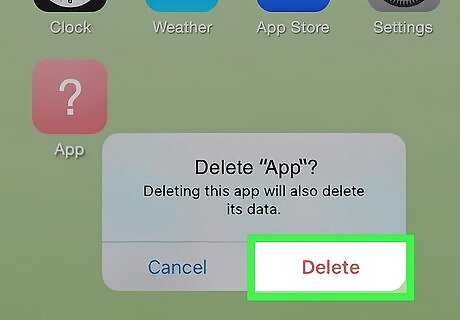
Delete unrecognized apps. If you notice a suspicious app that you don't remember installing, delete it. You can delete these apps directly from the home screen, or you can navigate to Settings and then Apps to view all the apps installed on your phone. Make sure to fully delete the app. If the app is on your home screen and you try to delete it, your phone will ask if you want to remove it from the home screen only or fully delete it. Be sure to delete the app, as removing it from the home screen keeps it installed on your device.
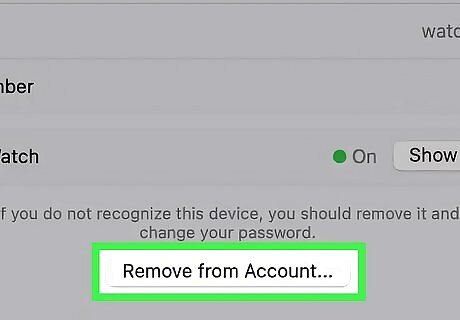
Remove unrecognized devices. If there are unrecognized devices that have access to your Apple ID, you should remove them. You should also remove old devices that you don't have anymore to reduce the chance that someone accidentally logs into your Apple ID. Sign in at appleid.apple.com and select Devices on the left-hand side. Select any unrecognized device and click Remove from account. The site will ask you for confirmation, so click through until the device has been removed.

Run an antivirus scan. Just like your computer, you can run antivirus on your iPhone. If there is malicious software on your phone, an antivirus scan can help identify, quarantine, and remove it. If you already have antivirus for your computer, check to see if there is an associated mobile app for the company you use. Some antivirus providers have bundles for their computer client and mobile app.

Update your phone and apps. Phone updates can be tedious, but keeping your phone and apps up-to-date ensures the newest safety measures are installed on your device as well. Updating your phone and apps can fix security breaches that hackers use to get into your device.

Report the fraud to Apple. If your Apple ID or iCloud has been compromised, you should contact Apple Support to report the fraud. Note that Apple won't contact you for any reason unless you contact them first, so if Apple contacts you directly this is a scam you should avoid. You can notify Apple via the following methods: Email: [email protected] Phone: 800-275-2273 In person: Visit any Apple Store and ask to speak to a customer support representative
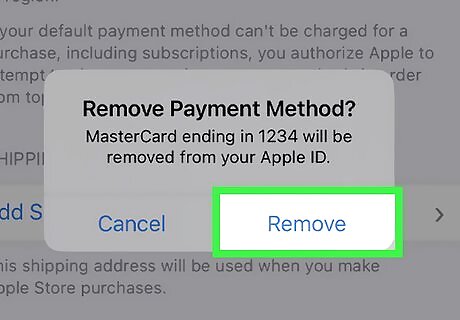
Cancel any cards linked to your device. If you had a credit or debit card linked to your Apple Pay, you may want to have those cards canceled and reissued. You can call your bank or credit provider and explain the situation before asking if those cards can be reissued with new numbers.
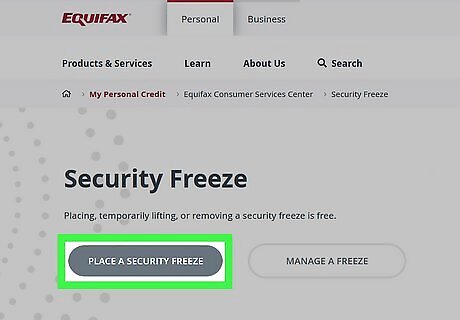
Freeze your credit. If you suspect your personal information has been stolen, you can place a credit freeze with the three major credit bureaus. This keeps a hacker from using your personal information to apply for loans or open new accounts. To freeze your credit you need to contact each bureau individually: Equifax: 1-800-349-9960 or online Experian: 1-888-397-3742 or online TransUnion: 1-888-909-8872 or online
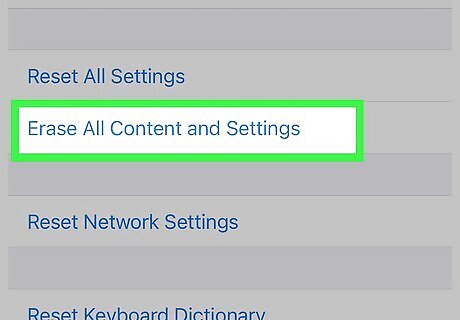
Factory reset your iPhone. Factory resetting your phone is a last resort, but if you've tried the other methods listed above and your phone is still showing signs of being hacked, this is a surefire way to get a hacker out of your phone.
How to Avoid Getting Hacked
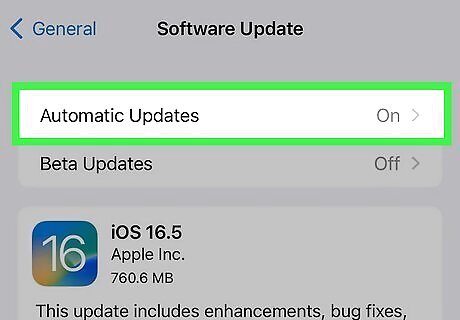
Keep your phone's OS up-to-date. iOS updates will sometimes include fixes to security vulnerabilities. If you don't update your phone often, your phone will eventually end up having security holes that a hacker can get through.
Use complex passwords and passcodes. If someone does get into your phone, having complex passwords can help keep the hacker away from your sensitive information. You should create long passwords that are hard to guess, and don't use the same password for every account you have.
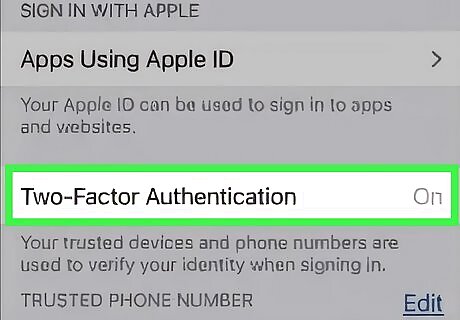
Set up two-factor authentication (2FA) on your Apple ID. Adding 2FA to your Apple ID means hackers can't access Apple services with your ID without you knowing. Navigate to Settings and click your name at the top of the screen. Select Password & Security. Near the top of the screen, turn Two-Factor Authentication on.
Learn how to identify phishing scams. Phishing scams are when a hacker sends a malicious link to you in hopes that you'll click it so they can get some information out of you. Scammers will send emails, texts, phone calls, calendar invites and more with these phishing links.
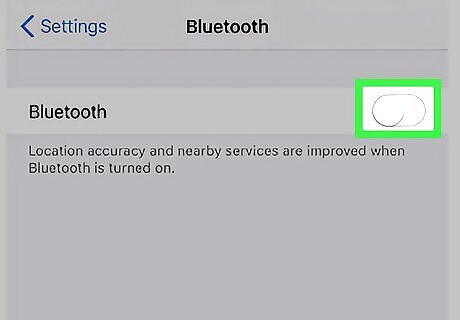
Turn off Bluetooth if you're not using it. If you're in public and your phone is actively looking for Bluetooth devices, hackers can use this to get into your phone. If you're not actively using your Bluetooth, turn it off to keep hackers at bay. You can easily turn off Bluetooth by swiping down from the top right of your phone screen and tapping the Bluetooth button in the top left corner. You can also turn off Bluetooth by going to your iPhone Settings app and selecting the Bluetooth menu item near the top. In this menu you can toggle Bluetooth on or off.

Don't jailbreak your phone. Jailbreaking means to modify your iPhone to remove certain restrictions placed by Apple, usually to install unauthorized apps or software on the phone. This can be a huge security risk as you won't be able to update your iOS conventionally, which means your phone can miss out on the security exploit fixes provided by the update.
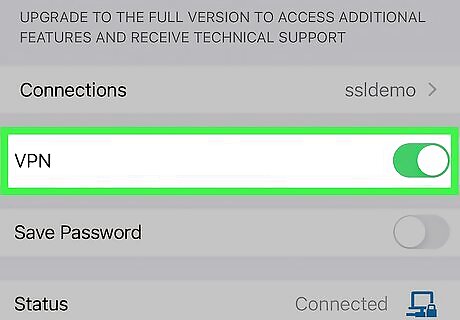
Use a VPN. Just like on a computer, you can use a VPN on your phone. A VPN, or virtual private network, allows you to connect to the internet more securely by encrypting your connection. If you already use a VPN provider for your computer, you may want to use the same VPN for your phone. Just like with antivirus, some VPN providers may offer bundles for computers and phones.
How iPhones Get Hacked

Insecure Wi-Fi networks. While public Wi-Fi networks are very convenient, they may not be secure. And if you're in a populated area, there could be a lot of people on any given public Wi-Fi network, including people with malicious intentions. Connecting to an insecure Wi-Fi network could leave your phone open to hackers.
Suspicious apps. Sometimes hackers will utilize apps to gain access to your device. If an app seems suspicious to you, don't install it. Only install apps you trust, and check the reviews before downloading any app.
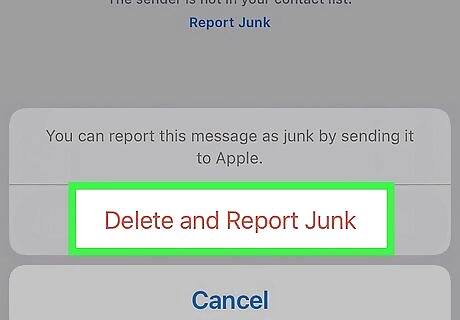
Phishing links in texts, emails, and calendar invites. Hackers may try and get you to click on links or accept calendar invites that could swipe your information or allow the hacker access to your device. Avoid any suspicious links, and report phishing scams to Apple as you encounter them.

Security gaps in jailbroken phones. If your phone is jailbroken, there could be major security vulnerabilities in your device that hackers can take advantage of. Don't jailbreak your phone, and if it's already jailbroken you can restore your phone to factory settings.

Zero-day patch exploits. While keeping your phone updated is important, sometimes hackers can take advantage of security exploits the first day that a new iOS patch is available. If you are concerned about zero-day patch exploits, you can wait a few days after a new iOS version is available to wait for any security hotfixes.




















Comments
0 comment