views
With the arrest of four terrorists of Pakistan-based terror outfit Jaish-e-Mohammed (JeM), a major terror plot to target the Ram Janmabhoomi Temple in Ayodhya and the Panipat refinery has been foiled by the Jammu and Kashmir police.
The four JeM terrorists arrested from Jammu were in touch with Jaish commanders in Pakistan, who had deputed one of the four, identified as Ijahar Khan of Shamli in Uttar Pradesh, to carry out the reconnaissance of Ram Janmabhoomi in Ayodhya and Panipat refinery. However, the Jammu and Kashmir police busted the module before it could carry out the attacks.
“For past 20 to 25 days, we were working on the Jaish module. In Pakistan, there is a JeM commander named Shahid, also known as Munzir. He was the one behind the module. This module has large number of terrorists. So far we have arrested four. One is from UP and three from Kashmir,” said Mukesh Singh, Additional Director General of Police, Jammu.
The police in Jammu busted a Jaish-e-Mohammed module and arrested four terrorists who were planning to carry out major terror strikes across the country on and before the Independence Day celebrations.
“Four Jaish terrorists and their associates have been arrested by Jammu police in a drive to root out terrorist presence in Jammu. They were planning collection of arms dropped by drones and supply to active terrorists of Jaish-e-Mohammed in Kashmir valley; planting a vehicle-based IED in Jammu before August 15 and reconnaissance of important targets in other parts of the country,” Singh said.
He said that the Jammu police first arrested JeM’s Muntazir Manzoor alias Saifulla of Prichoo Pulwama and recovered one pistol, one magazine, eight live rounds and two Chinese hand grenades from his possession. His truck used for transporting weapons to the Kashmir valley was also seized.
The officer said based on leads provided by Manzoor, the other three terrorists were arrested. One was apprehended from the Shamli area of Uttar Pradesh.
“Ijahar Khan alias Sonu Khan of Mirdan Mohalla Kandala, Shamli (UP) was arrested and he disclosed that the Jaish commander in Pakistan namely Munazir alias Shahid had asked him to collect weapons from near Amritsar which would be dropped by a drone. He was also asked by Jaish to do reconnaissance of Panipat oil refinery which he did and sent videos to Pakistan. He was then tasked to do the reconnaissance of Ayodhya Ram Janmabhoomi but was arrested before he could accomplish this task,” Singh said.
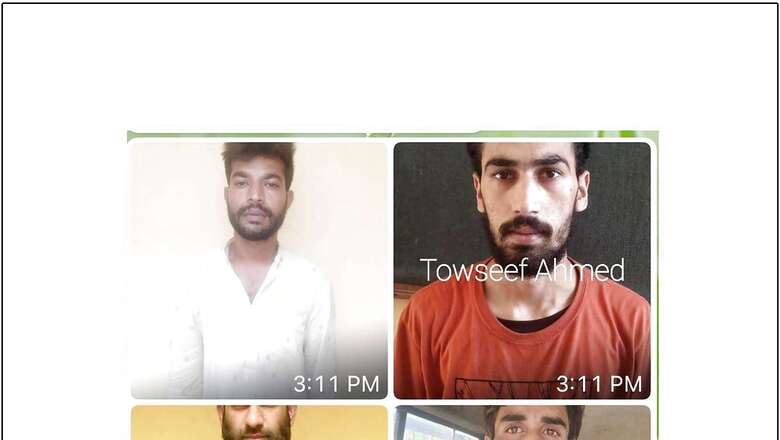
He said that another arrested terrorist identified as Touseef Ahmed Shah alias Showket alias Adnan of Jeff, Shopian was tasked by Jaish commander Shahid and another Jaish terrorist by the name Abrar in Pakistan to take up an accommodation in Jammu, which he did.
“He was then asked to procure a second hand motorcycle for causing an IED blast in Jammu. The IED for this purpose would be dropped by a drone. Touseef was arrested before he could complete this task,” he said.
He said that the fourth terrorst, identified as Jahangir Ahmed Bhat of Bandzoo Pulwama who also was arrested, is a fruit merchant from Kashmir. He was constantly in touch with Shahid in Pakistan and had introduced Ijahar Khan to him.
“He was further recruiting for Jaish in the Kashmir valley and in the rest of the country,” the officer said.
The officer further revealed that with the arrest of the four Jaish-e-Mohammed terrorists by the Jammu police a major terror plot has been busted.
“The questioning of all the four terrorists is going on and we expect more arrests in the coming days,” he said.
Read all the Latest News, Breaking News and Special: Live-updating IPL 2022 auction tally | IPL Mega Auction Live Updates here.




















Comments
0 comment